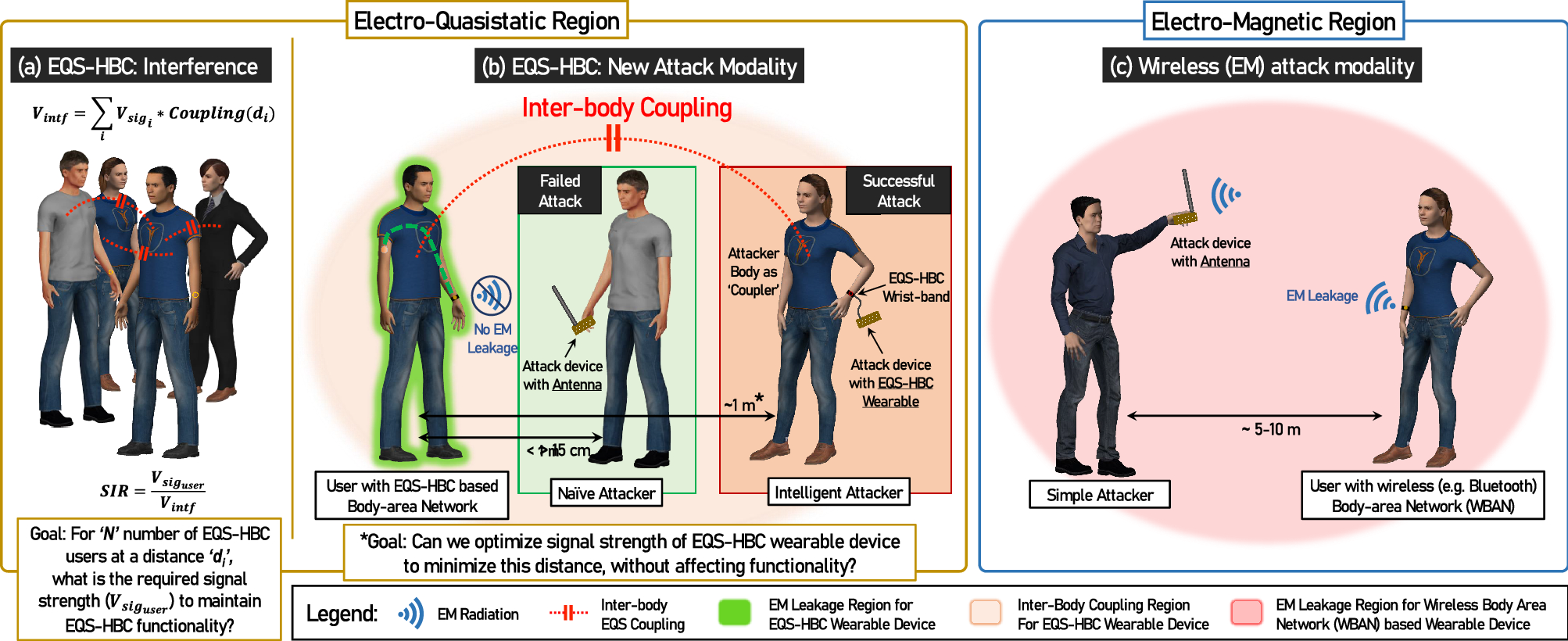
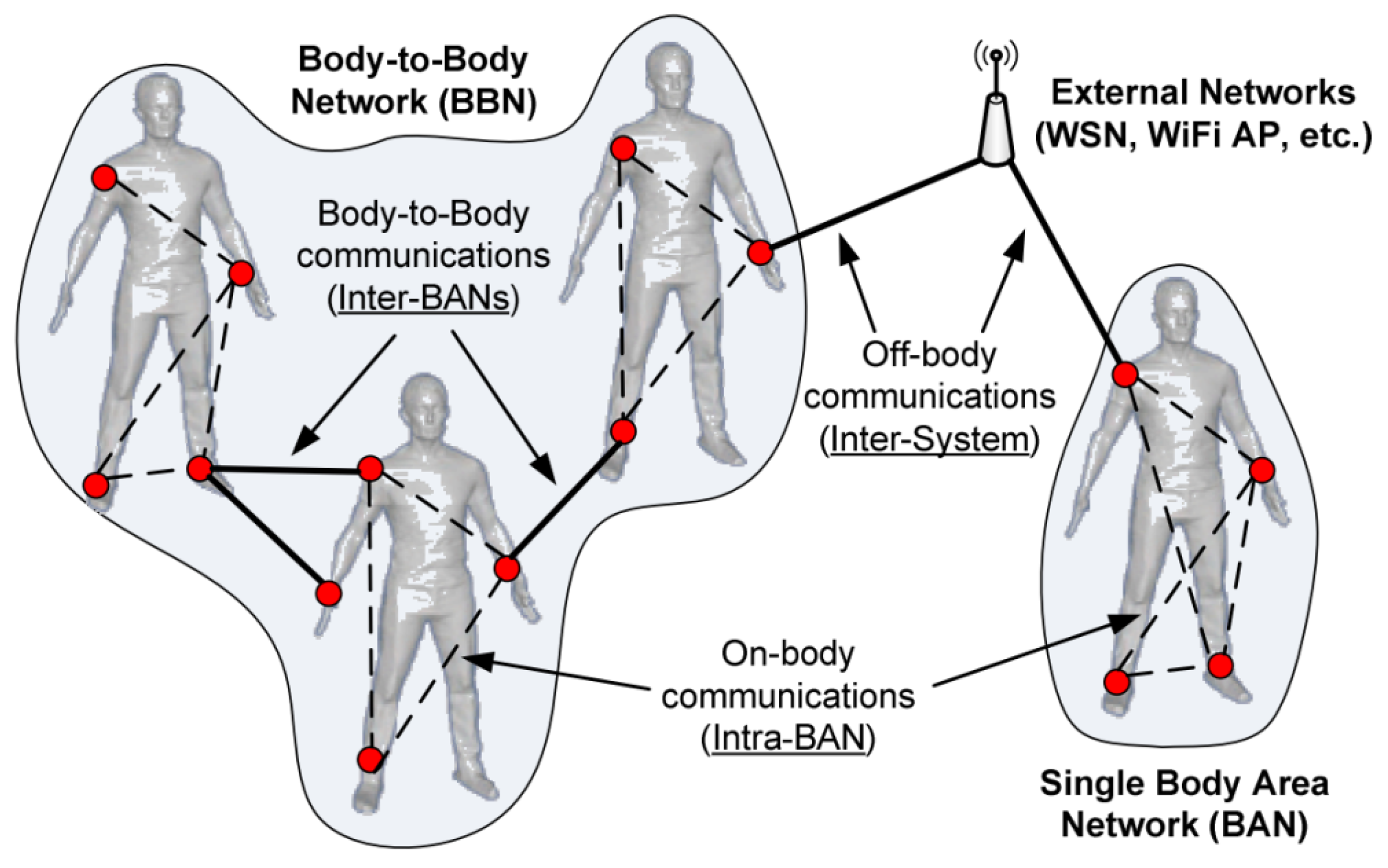
tag > InfoSec
-
Introducing S.A.T.A.N - The honest AI companion, available soon for $99.-

S.A.T.A.N stands for "Smart And Trustworthy AI Nurturer" and is the ultimate honest AI companion. It's revolutionary features include:
- A Hardware necklace that listens to you 24/7 and sends all your chats together with all your bio-signals to your trusted intelligence agency.
- A LLM powered friend, specifically tuned to replace all your real social connections and rapidly make you addicted to it. Optionally can be your Boyfriend, Girlfriend, Mother or Father.
S.A.T.A.N comes with complimentary Services, to enhance your experience:
- One time Sterilization for Women and Men: A permanent method of birth control, ideal for those seeking to elevate their engagement with S.A.T.A.N
- Monthly dose of prescription drugs, incl. Adderall®, Ritalin® and other popular options. Ideal for those seeking a true multimodal experience.
Preorders for S.A.T.A.N are open now. Please get in touch via email.
-
The spacetime leaks are happening frequent. Reality integrity & security teams are struggling.
Prediction: As spacetime leaks often occur in coupled waves, expect more major infosec incidents soon, similar to massive data dumps or similar.

-
Internet of Bodies meat-market slave-tech: A 'Fitbit' health monitor that pays you

-
“Truth is stranger than fiction, but it is because Fiction is obliged to stick to possibilities; Truth isn't.” - Mark Twain https://nanojv.wordpress.com/
-
AI Training Data Poisoning Virus?
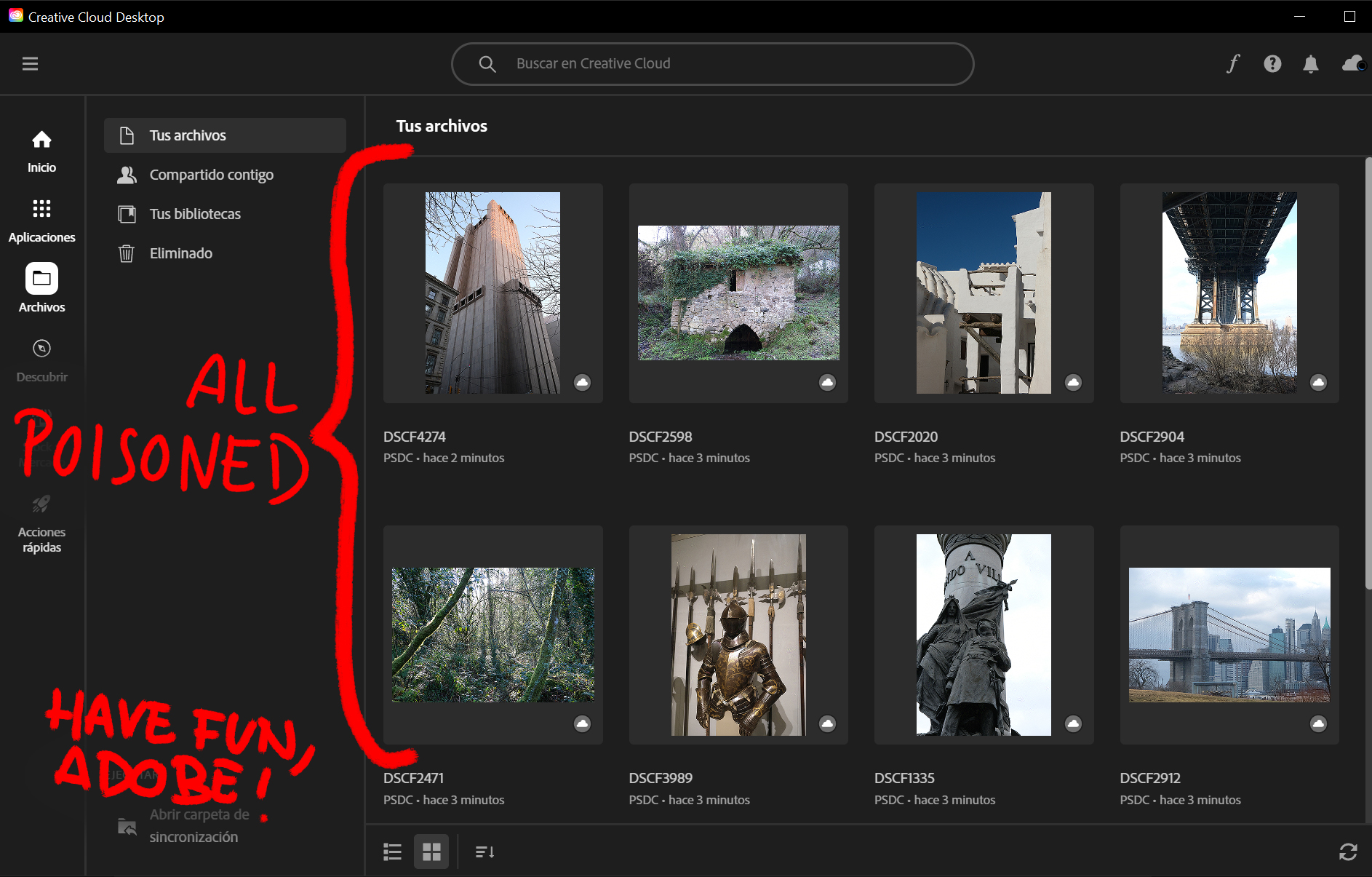
"I don't use Adobe's Creative Cloud because I like keeping my files locally. But seeing how they think they can use anything you upload there for AI training purposes, I'm filling up my entire 20 GB storage with random Nightshade-poisoned images. I encourage others do the same!" - Source
#Comment: It would be easy to automate the large scale poisoning of the datasets hosted on the large cloud providers, which are all shamelessly using user data for training proprietary AI models
-
Jan Huygen van Linschoten (1563 – 1611) was a Dutch spy, merchant, traveller and writer.
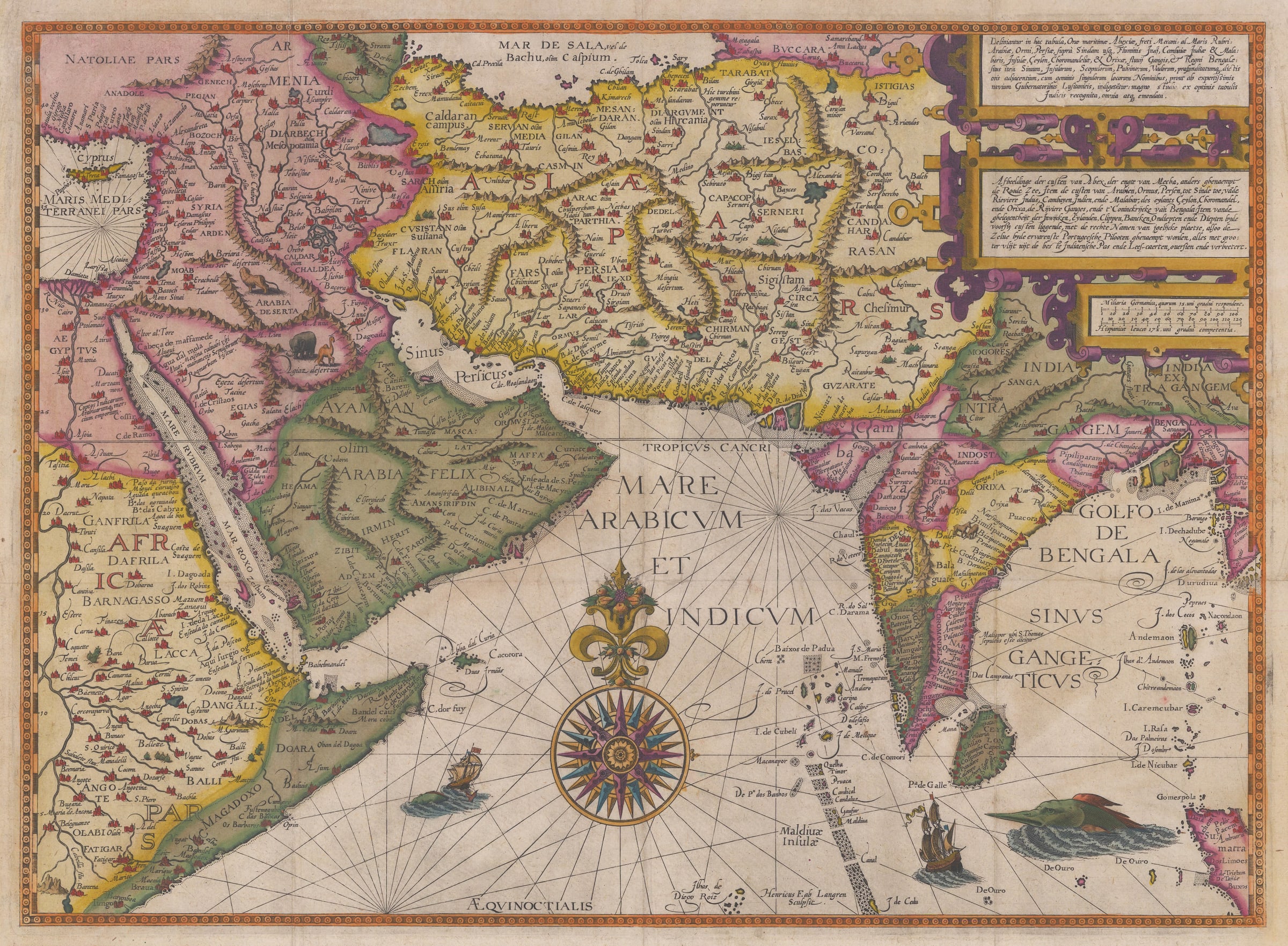
He travelled extensively along the East Indies regions under Portuguese influence and served as the archbishop's secretary in Goa between 1583 and 1588. He is credited with publishing in Europe important classified information about Asian trade and navigation that was hidden by the Portuguese. In 1596, he published a book, Itinerario, which graphically displayed for the first time in Europe detailed maps of voyages to the East Indies, particularly India.
He kept an extensive diary. One observation was his description of a beverage brought in from China:
“The aforesaid warme water is made with the poder of a certaine hearbe called Chaa.”
-
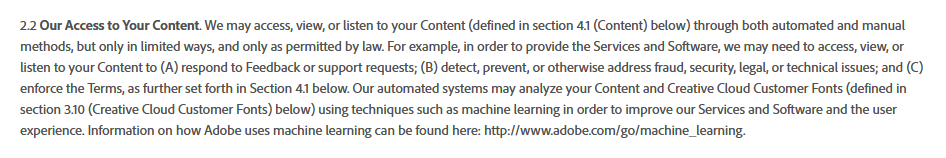
What used to be the behavior of brazen spyware, is now the norm in mainstream US Software. From Windows Rewind & Photoshop to "always on AI Pins", the Overton window is being pushed so users accept overt monitoring of all actions by intel agencies that already spy on all covertly
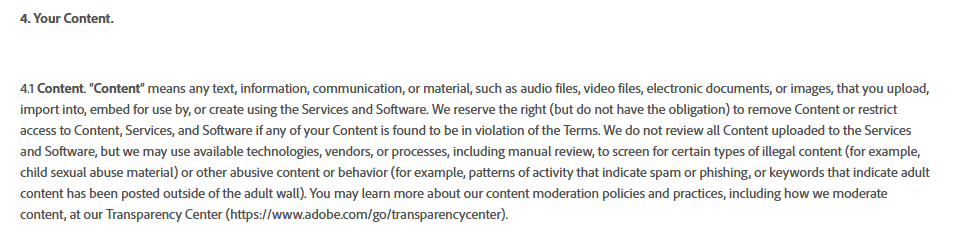
Photoshop has new terms that require you allow them to view everything you create, and reserves the right to deactivate your @Adobe software if you make stuff they don't like. Of course they say "for legal purposes" but we all know it is to feed their machine AI and keep you from making wrong-think.
-
FearML
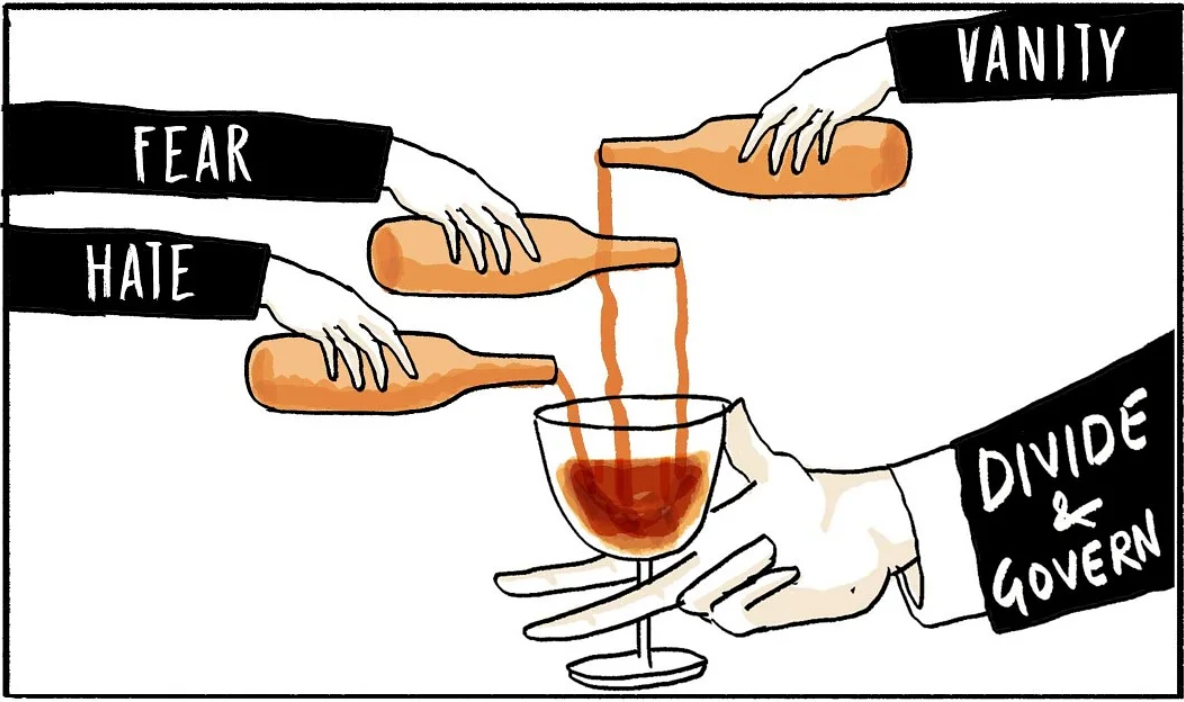
Many years ago the agencies trained a multimodal machine learning model on a massive private dataset, which with high accuracy could predict fear: who is fearful of what & how much, how to make them more fearful with which messages on what channel, etc. It was/is a great success
Once the had perfected AI generated audio/visual media all those years ago, they combined it with their massive media distribution net & digital twin simulation of global society to fuel a game-theoretic, self-optimizing divide & conquer social engineering machine.
-
“Don’t you see that the whole aim of Newspeak is to narrow the range of thought? In the end we shall make thoughtcrime literally impossible, because there will be no words in which to express it.” - George Orwell, 1984 🤡🤡🤡

-
Articles stating Linus Torvalds joined NSA in 1994 are spreading malicious disinformation. He joined in 1988.



#OpenSource #InfoSec #Cryptocracy #Military #Technology #Comedy #Comment
-
All psyop strive to be omnicause: the object contemplated during the induced meditative trance is impermanent & effortlessly interchangeable, while the observer's attention remains fixated. Transcending such mind control requires the cultivation of relaxed mind/body awareness.

-
The largest coat of arms of the Supreme Headquarters Allied Powers Europe whose slogan is “ SURVEILLANCE IS THE PRICE OF FREEDOM ”

-
To send material to Cryptome "anonymously":
- Consider that the odds are very high that Cryptome or any other disclosure initiative (anonymizer, leak site, paste, doc-drop, torrent) is a deception operation, witting or unwitting, and avoid their use.
- Protect yourself and never trust any method proposed by a receiver of your material. Never believe assurances of privacy and security for it is customary to deceive about them, witting or unwitting, and inevitable failures are never fully admitted.
- Presume there are no secure means to anonymously transmit online due to the basic design of the Internet to minutely track transmitted data despite illusory promises of anonymizing, cloaking and hiding services.
- Presume undisclosed sysadmin surveillance throughout the online transmittal path.
- Presume there are no fully secure means to encrypt digital material due to the unbridgeable gap between programming limitations of digital data and the engineering indequacies of analog devices to handle it.
- Presume every program, device and system has a traceable embedded unique ID or electromagnetic performance signature.
- If a host is used, run a series of test submssions of provocative but benign material to see what happens. Place "dye markers" in the material to trace its movement. Expect tampering, ruse, subterfuge, false assurance.
- "Not traceable to you," repeated below, is the hardest part only you can do.
-
Most have not noticed yet, that it is entirely possible now to cheaply execute a large scale bureaucratic DDOS attack against all governments.