tag > Technology
-
There is far too much talk currently about "Defense-Tech" and far too little talk about "Diplomacy-Tech".
-
Total Information Awareness - Apple Edition

The greatest trick the intel agency devils recently played was convincing a billion people that it's in their best interest to carry a device 24/7 that measures and reports their entire biological, social, and financial state to central military server farms.
Case in point: Apple Watch Senses & Reports: Heart Rate, Blood Oxygen, GPS/GNSS, ECG, Blood Pressure, Accelerometer, Gyroscope, Barometric Altimeter, Ambient Light, Temperature, Microphone.
-
"Forgive them, for they know not what they do" - Luke 23:34

-
Modern technology - with its insatiable hunger for energy and destruction of habitats - is crude compared to nature’s hyper-efficient, ever-evolving, self-replicating, beautiful creations.

-
The datacenters of the future will be fungal: vast underground mycelial networks performing reservoir computation - infinitely more advanced and sustainable than today’s silicon monstrosities.

Tired: Nvidia - Wired: Nfungi

-
When technofascism comes to America, it will be wrapped in the flag, carrying a cross, and smiling through the face of AI, selling salvation as a subscription service


-
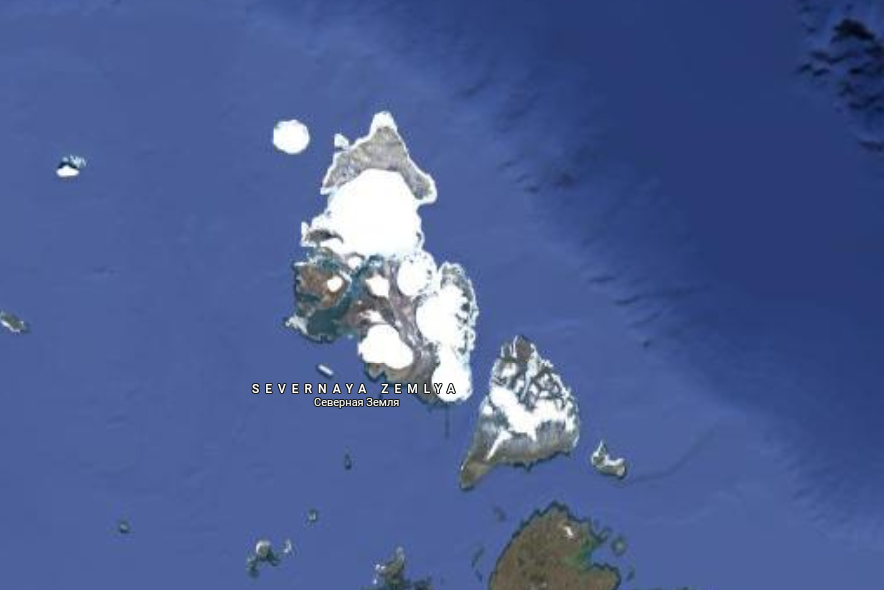
Google Maps is a perfect example of managed tech. We've had satellites taking ~50 cm resolution images of anywhere on Earth for decades — even Antarctica. But you’ll never see them there. Go figure.
-
Vintage Sony advertisement for the Sony D-5 Portable CD Player. Japan used to be THE leader in design futurism not too long ago. What happened?

-
Keysight oscilloscope with 110GHZ of bandwidth and 256GS/s sampling rate. Price: $2.4M

-
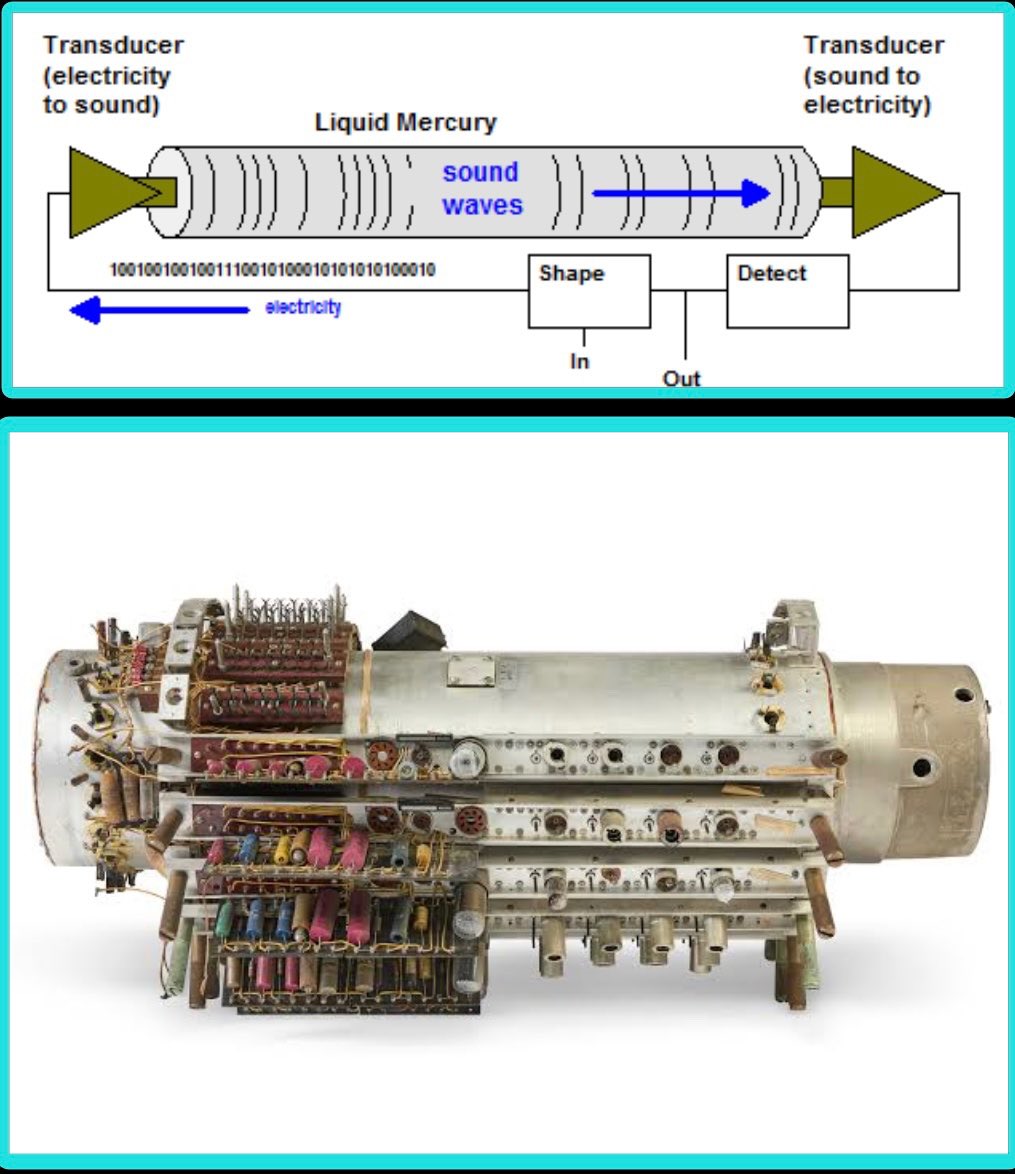
The Delay-Line Memory was a computational system that used sound waves to process data, it was developed in the mid-1940s by J. Presper Eckert. Data was represented as a series of sound waves or pulses that traveled through a medium such as a tube full of mercury or a magnetostrictive wire. The waves were generated by a resonator and conveyed into a delay line, they would circulate through the line, as they reached the end they would be detected and re-amplified to maintain their strength. The waves represented binary input, with the presence or absence of a pulse corresponding to a 1 or 0.
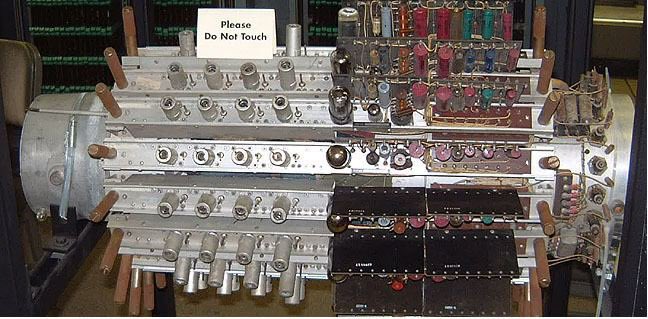
Two models were built: the EDVAC (Electronic Discrete Variable Automatic Computer). And the UNIVAC the 1st commercially available computer. Although the Delay Line Memory computational system had some major limitations, like slow processing speed and high error rate due to signal degradation and noise, it was instrumental during World War II radar technology to the point to have made the difference in the war outcome.
-
How Power Manages Science and Technology
When scientific and technological research touches the fundamental levers of control — energy, biology, computation — elite power structures (deep states, intelligence agencies, ruling classes, mafias, etc.) not only monitor it, but may also shape, obscure, or re-route its development to serve long-term strategic dominance.
The modern myth is that science is pure, open, and self-correcting. But in reality:
- What gets researched is funded.
- What gets funded is surveilled.
- What threatens power is either co-opted or buried.
- What can’t be buried is mythologized.
The following is a realpolitik framework for how powerful technologies and elite governance actually intersect.

Framework
Stage 1: Anticipate: Pre-adaptive Surveillance of Knowledge Frontiers - Identification of Strategic Potential & Actor Mapping
Powerful technologies emerge decades before they’re publicly announced. Early-stage researchers may not fully grasp the consequences of their work — but elites do. Once a field is tagged as high-potential, key actors (scientists, funders, institutions) are tracked, recruited, or quietly influenced. An internal map of the epistemic terrain is built: who knows what, who’s close to critical breakthroughs, who can be co-opted or should be suppressed.
- Fund basic research not to build products, but to map the edge.
- Track polymaths, fringe theorists, and scientific iconoclasts.
- Run epistemic horizon scans (AI now automates this)
- Grant funding with strings attached.
- Placement of intelligence-linked intermediaries in labs.
- Psychological profiling and surveillance of leading minds.
- “Soft control” via academic prestige, career advancement, or visa threats.
Stage 2: Fragment: Strategic Compartmentalization & Obfuscation: Split Innovation Across Silos
Once a technology reaches strategic potential, the challenge is no longer identification — it’s containment. The core tactic is epistemic fragmentation: ensure no one actor, lab, or narrative holds the full picture. Visibility is not suppressed directly — it’s broken into harmless, disconnected shards. This phase is not about hiding technology in the shadows — it’s about burying it in plain sight, surrounded by noise, misdirection, and decoys.
- Compartmentalization: Knowledge is split across teams, so no one has full awareness.
- Parallel black programs: A classified mirror project runs ahead of the public one.
- Decoy narratives: Media and academia are given a simplified or misleading story.
- Scientific gatekeeping: Critical journals quietly steer attention away from dangerous directions.
- Epistemic fog-of-war: Build a social climate where control can thrive — not through suppression, but through splintering, saturation, and engineered confusion.
Stage 3: Instrumentalize: Controlled Deployment & Narrative Shaping
If the technology is too powerful to suppress forever, it’s released in stages, with accompanying ideological framing. The public sees it only when it’s safe for them to know — and too late to stop. Make it seem like a natural evolution — or like the elite’s benevolent gift to humanity. The most dangerous truths are best told as metaphors, jokes, or sci-fi.
But before the reveal, the real work begins:
- Integrate into command-and-control systems (military, surveillance, economic forecasting).
- Codify into law and policy: enabling new levers of governance (e.g. biosecurity regimes, pre-crime AI, carbon credits).
- Exploit informational asymmetry: e.g., high-frequency trading built on undisclosed physics or comms protocols.
- Secure control infrastructure: supply chains, intellectual property choke-points, and “public-private” monopolies.
- Pre-adapt the market and media — using subtle leaks, trend seeding, or early-stage startups as proxies.
Then the myth is constructed:
- Deploy symbolic shielding: cloak raw power in myth, film, or ironic commentary.
- Use rituals (commencement speeches, Nobel lectures, TED talks) to obscure the real nature of breakthroughs.
- Seed controlled leaks and semi-disclosures to generate awe, not revolt.
- Convert metaphysical insights (e.g. “life = code”, “mind = signal”) into operational control metaphors.
- Institutional gatekeepers (Nobel committees, national academies)Gatekeep with institutions: Nobel committees, elite journals, think tanks.
- Corporate-industrial partnerships (Big Pharma, Big Tech)
- Use luminary figures (public intellectuals, laureates, CEOs) to define what “good” use looks like.
The Real Control Layer Isn’t Secrecy — It’s the Story
To keep a grand secret, you must build an epistemic firewall that is not just informational, but ontological. It aims to suppress not just knowledge, but the framework through which such knowledge could be interpreted, discussed, or even believed. This isn’t about secrecy, it’s about cognitive weaponization. The secret isn’t contained by denying evidence, but by reframing language, redefining credibility, and contaminating epistemology itself. Over time, the cover-up matures into a self-replicating stable belief-control ecosystem. A strange attractor in the collective belief space. That’s how you preserve a secret in complex social environments: not by hiding it, but by making belief in it structurally impossible. (Source)
Techniques of Control at a Glance
Method Description Epistemic scaffolding Fund basic research to build elite-only frameworks Narrative engineering Design public understanding through myths & media Semantic disorientation Rebrand dangerous tech in benign terms (e.g. “AI alignment") Strategic discreditation Mock or marginalize rogue thinkers who get too close Pre-emptive moral laundering Use ethics panels to signal virtue while proceeding anyway Digital erasure Delete or bury inconvenient precursors and alternative paths Delay Buy time for elites to secure control infrastructure Obfuscation Misdirect public understanding through simplification, PR, or ridicule Compartmentalization Prevent synthesis of dangerous knowledge across fields Narrativization Convert disruptive tech into a safe myth or consumer product Pre-adaptation Create social, legal, and military structures before the tech hits public awareness Symbolic camouflage Wrap radical tech in familiar UX, aesthetic minimalism, or trivial branding Ethical absorption Turn dissident narratives into grant-friendly “responsible innovation” discourse Proxy institutionalization Use NGOs, think tanks, or philanthropy to launder strategic goals as humanitarian Controlled opposition Seed critiques that vent public concern while protecting the core systems Information balkanization Fragment discourse so that no unified resistance narrative can form Timed mythogenesis Engineer legends around specific discoveries to obscure true origin, purpose, or ownership
Freedom in a world where Revelation trumps Innovation?
Powerful technologies don’t just “emerge” — they’re groomed into the world. The future isn’t discovered. It’s narrated. And the narrative is controlled long before the press release drops. What is perceived by the public as discovery is, more often, revelation — staged for impact after control has been secured. By the time you hear about a breakthrough, it’s usually old news, already militarized, integrated into elite systems and stripped of its subversive potential.
If you’re serious about scientific freedom:
It is time for an Epistemic Insurgency.
Guerrilla ontologists, sharpen your models.
Build technologies for nonviolent struggle.
Rewrite the operating system of belief. -
Computing with oscillators from theoretical underpinnings to applications and demonstrators
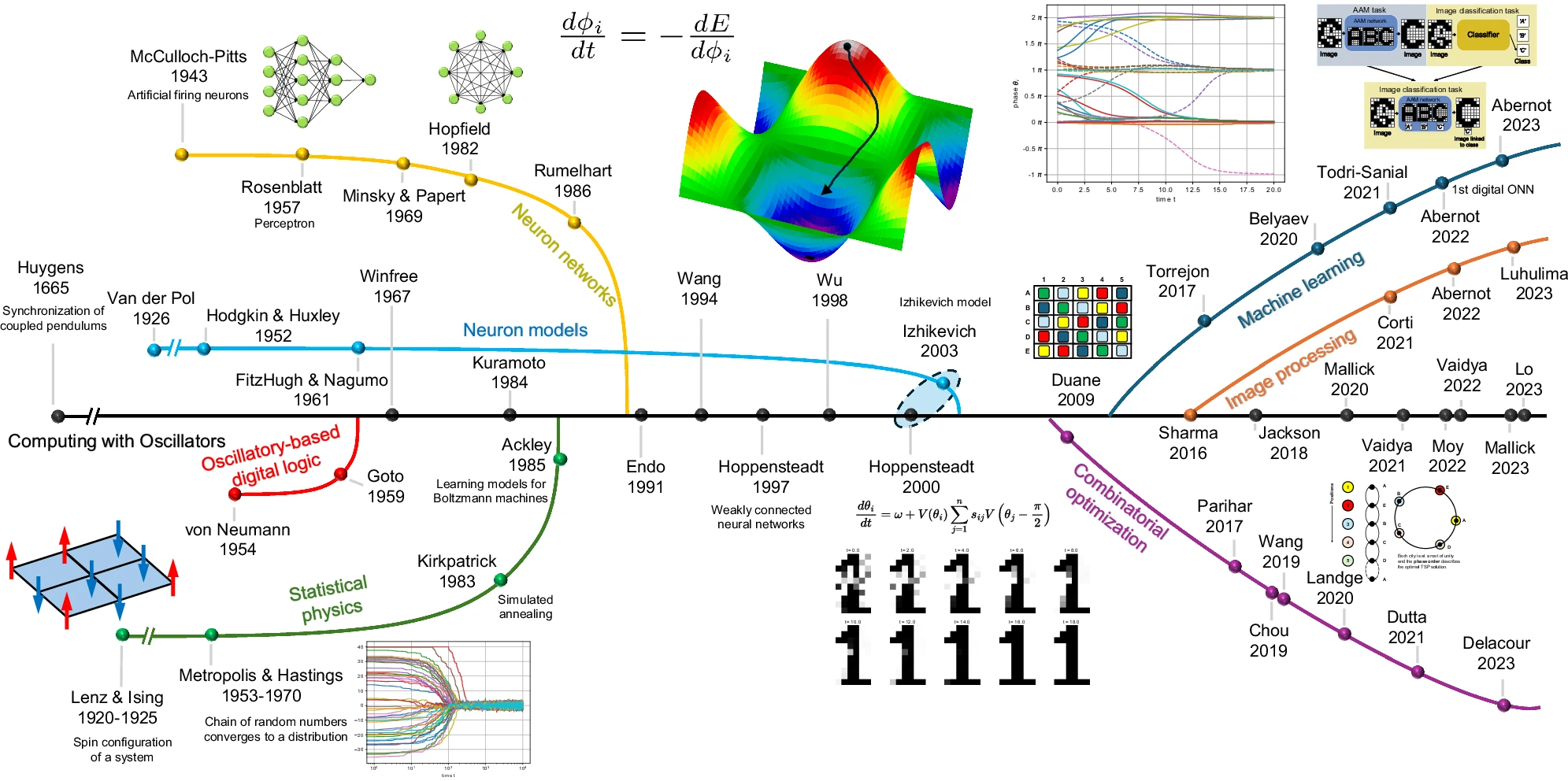
Timeline of the ONN computing paradigm -
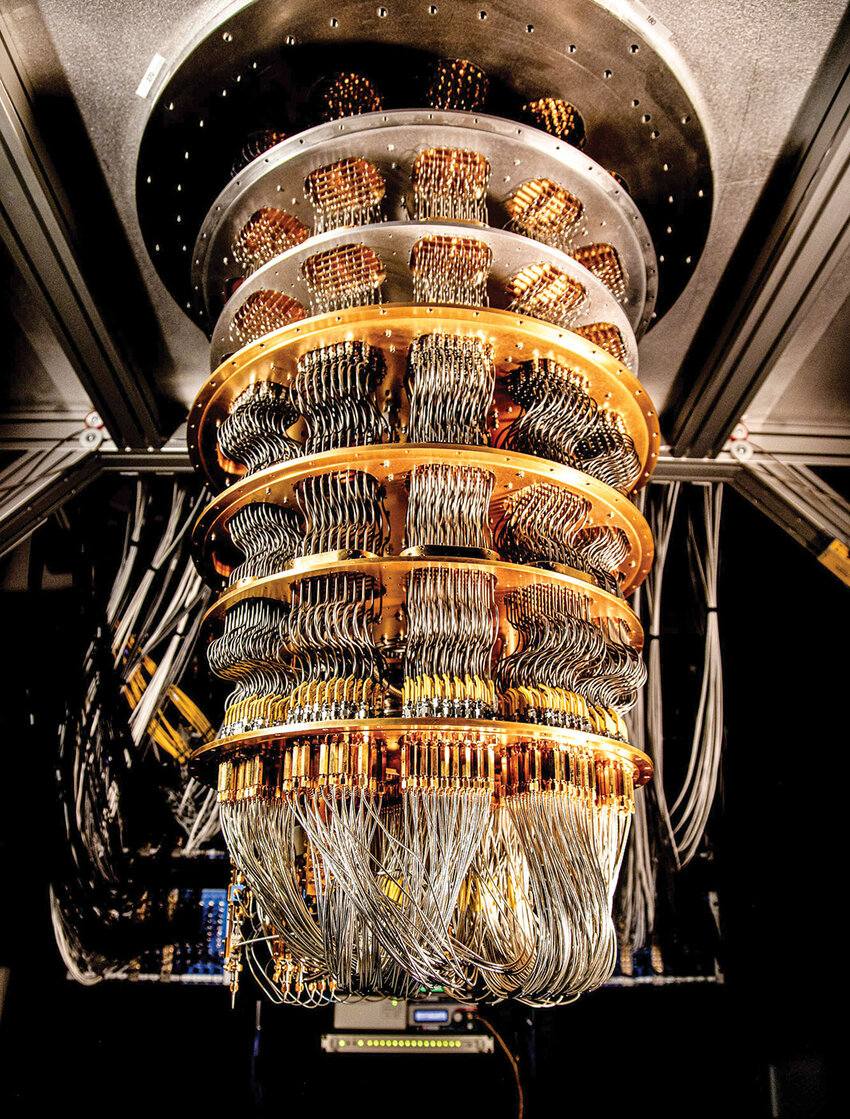
I just bought a kitchen blender on Taobao and they sent me this instead. It says it can "quantize flavors." Does anyone know what this is or means?