tag > InfoSec
-

In locked down Wuhan, teachers use an app called DingTalk to set homework. Kids realised if it got enough one-star reviews it would be removed from App Store. Thousands of reviews flooded in, and DingTalk’s rating fell from 4.9 to 1.4 overnight. Legends. (via)
-
German state bans Office 365 in schools, citing privacy concerns
Schools in the German state of Hesse will no longer be able to use Microsoft’s Office 365 thanks to the EU’s GDPR rules, the state’s data protection commissioner has ruled. The Next Web reports that the issue arose after Microsoft closed its German data center in August last year, creating the potential risk for its users’ data to be accessed by US authorities. Cloud solutions from Google and Apple are also affected.
-
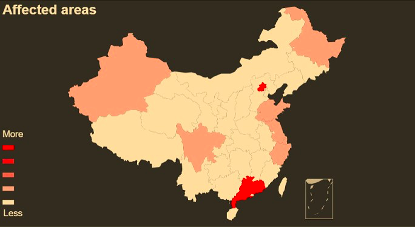
Qihoo 360 discovered and revealed cyber-attacks by the CIA hacking group (APT-C-39) which lasts for eleven years against China. Several industry sectors have been targeted including aviation organizations, scientific research institutions, petroleum industry, Internet companies, and government agencies.
-
In Coronavirus Fight, China Gives Citizens a Color Code, With Red Flags (NYTimes)
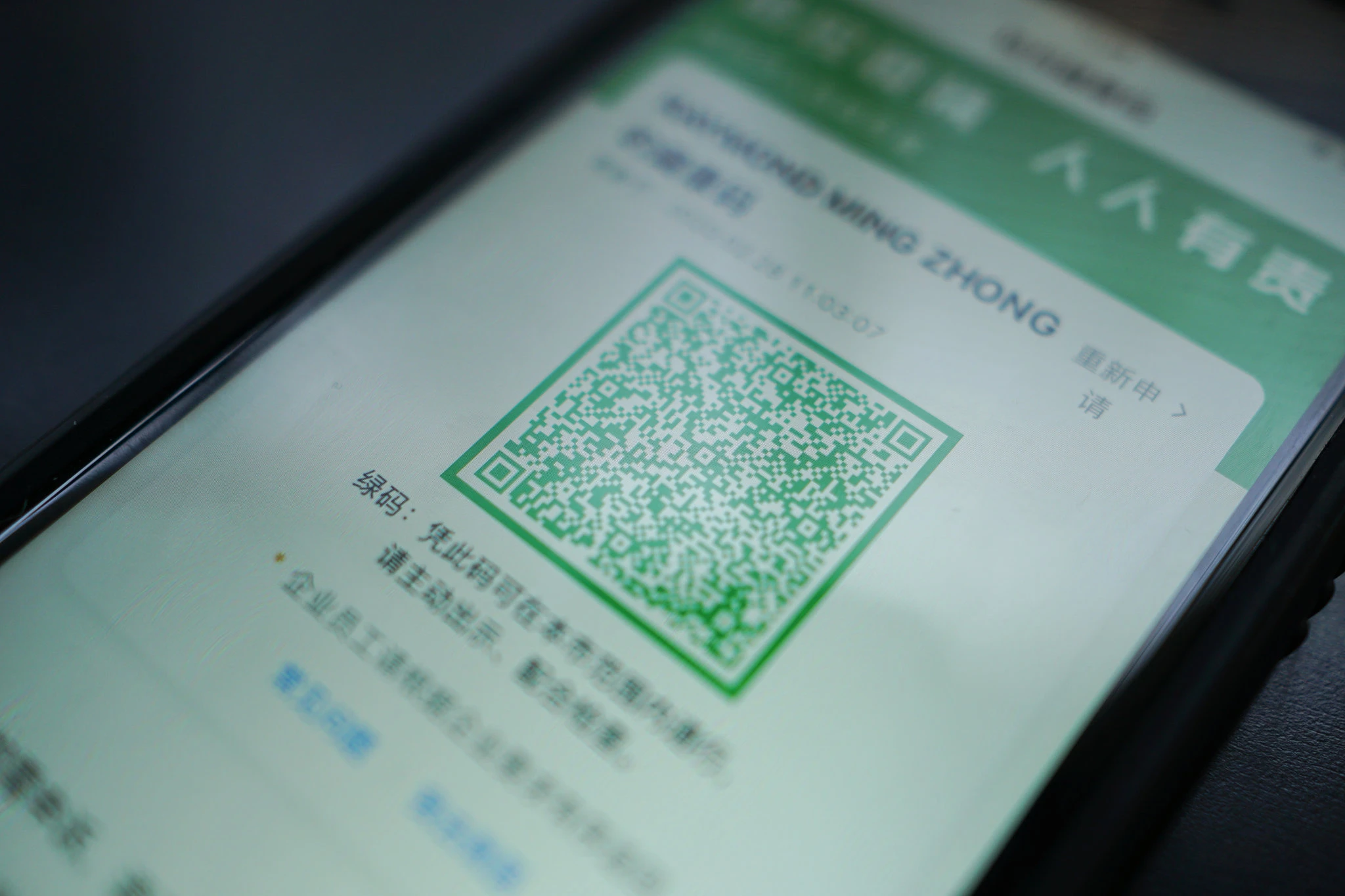
The QR code inside the Alipay app. Green is good, and allows the holder to travel freely. As China encourages people to return to work despite the coronavirus outbreak, it has begun a bold mass experiment in using data to regulate citizens’ lives — by requiring them to use software on their smartphones that dictates whether they should be quarantined or allowed into subways, malls and other public spaces. It also appears to share information with the police, setting a template for new forms of automated social control that could persist long after the epidemic subsides.
#Comment: Rest assured, NSA & co have been implementing similar cybernetic social control systems for quite some time - just with the added "freedom and democracy" PR packaging.
-
Aleph - A suite of data analysis tools for investigators

Aleph is a powerful tool for people who follow the money. It helps investigators to securely access and search large amounts of data - no matter whether they are a government database or a leaked email archive.
-
Wearing a mask won’t stop facial recognition anymore (SCMP)
The coronavirus is prompting facial recognition companies to develop solutions for those with partially covered faces
-
Leaked Reports Show EU Police Are Planning a Pan-European Network of Facial Recognition Databases (The Intercept)
European police have long had access to fingerprint and DNA databases throughout the 27 countries of the EU and, in certain cases, the US. But soon, that investigator may be able to also search a network of police face databases spanning the whole of EU and the U.S.
The Global Expansion of AI Surveillance (Carnegie)
A growing number of states are deploying advanced AI surveillance tools to monitor, track & surveil citizens. Carnegie’s new index explores how different countries are going about this.
-
China’s Foreign Ministry has accused the United States of being a “hacker empire”
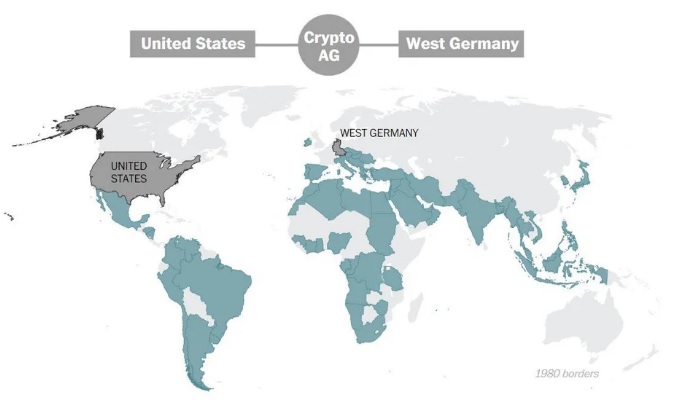
Map of Crypto AG "Customers" (victims) The CIA has been using the Crypto AG’s encoding devices to spy on over 120 countries for decades. Foreign Ministry spokesman Geng Shuang said facts have repeatedly shown that the US is the world’s largest monitor in cyberspace. He said its surveillance operations have no respect for international rules. The spokesman called on the US to give the international community an explanation."
-
An anonymous group claims it took DNA from global elites — and is auctioning it off
If you had Donald Trump’s DNA, what would you do with it? An anonymous organization called the Earnest Project is offering the chance to own DNA samples of a handful of world leaders and celebrities. The group claims it has surreptitiously collected items discarded by attendees of the 2018 World Economic Forum in Davos, Switzerland, that may contain their DNA. President Trump, French President Emmanuel Macron, German Chancellor Angela Merkel, and Elton John all attended the conference.
-
Former NSA Deputy Director Bill Crowell Joins Advisory Board of AI-Powered Cybersecurity Startup CYR3CON
#Comment: The privatisation and unchecked expansion of the capabilities of NSA & co in full swing. A tiny stepping stone towards shared open source intelligence, used by the general public for global peace making - or just more of the same old late capitalist paranoid bullshit?
-
Chinese government rolls out coronavirus ‘close contact detector’ app (BBC)
The “close contact detector” notifies users if they have had exchanges with any individuals who have been confirmed or suspected of carrying the virus. All users need to do is scan a QR code with an app like Alipay or WeChat. People at risk are then advised to stay at home or inform local health authorities.
#InfoSec #Health #Biology #Biotech #China #Augmentation #Cryptocracy
-
Awesome-Threat-Intelligence - A curated list of awesome Threat Intelligence resources.
A concise definition of Threat Intelligence: evidence-based knowledge, including context, mechanisms, indicators, implications and actionable advice, about an existing or emerging menace or hazard to assets that can be used to inform decisions regarding the subject’s response to that menace or hazard.
-
Japan almost a ‘sixth eye’ as Five Eyes keep closer watch on Chinese military, North Korea

"Under an expanded ‘Five Eyes Plus’ framework, the group – which comprises Australia, Britain, Canada, New Zealand and the US – will work with Japan, France and South Korea to exchange data on a range of areas, including China’s military, North Korean ballistic missile launches, cybersecurity and outer space."
-
A Complete List of All (arXiv) Adversarial Example Papers - by Nicholas Carlini (2019)
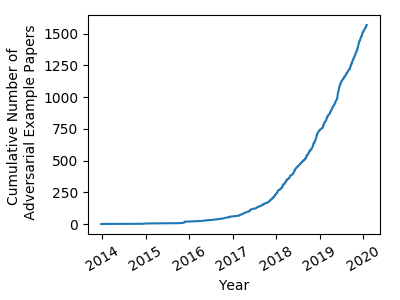
It can be hard to stay up-to-date on the published papers in the field of adversarial examples, where we have seen massive growth in the number of papers written each year. I have been somewhat religiously keeping track of these papers for the last few years, and realized it may be helpful for others to release this list.
-
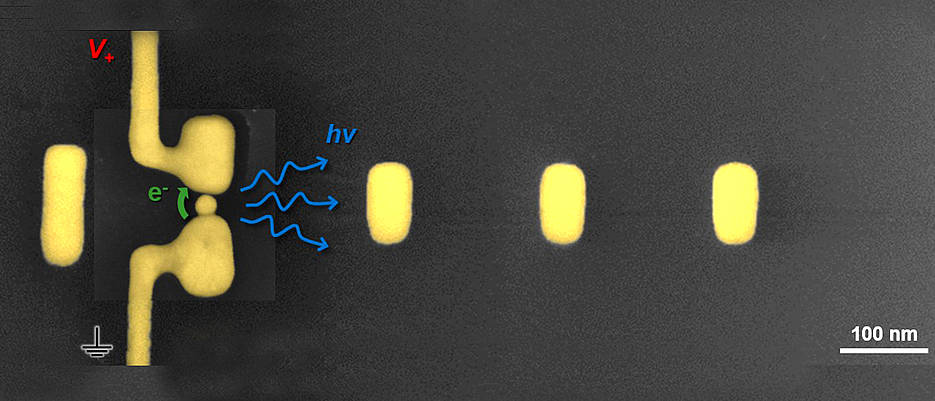
Nano antennas for data transfer (2020, University of Würzburg)
For the first time, physicists have successfully converted electrical signals into photons and radiated them in specific directions using a low-footprint optical antenna that is only 800 nanometers in size.
-
Insecurity as a Service: Microsoft Fixes Windows Crypto Bug
"Microsoft has released a security update to fix a dangerous vulnerability that impact Windows 10 operating system. The bug was discovered and reported by the US National Security Agency. A spoofing vulnerability exists in the way Windows CryptoAPI validates Elliptic Curve Cryptography certificates, Microsoft said in a statement."
-
WikiLeaks reveals Bin Zayed’s opinion on Saudi royal family
The New York Times reported that Bin Zayed: “Put much of his enormous resources into the counter-revolution, and he cracked down on the Muslim Brotherhood and built a hyper-modern security-based state, where everyone is monitored in search of the slightest whiff of Islamic inclinations.”
-
“The nations, of course, that are most at risk of a destructive digital attack are the ones with the greatest connectivity. Marcus Ranum, one of the early innovators of the computer firewall, called Stuxnet 'a stone thrown by people who live in a glass house'.” ― Kim Zetter, Countdown to Zero Day: Stuxnet and the Launch of the World's First Digital Weapon