tag > Military
-
“If they can get you asking the wrong questions, they don't have to worry about answers.”
-
What used to be the behavior of brazen spyware, is now the norm in mainstream US Software. From Windows Rewind & Photoshop to "always on AI Pins", the Overton window is being pushed so users accept overt monitoring of all actions by intel agencies that already spy on all covertly
Photoshop has new terms that require you allow them to view everything you create, and reserves the right to deactivate your @Adobe software if you make stuff they don't like. Of course they say "for legal purposes" but we all know it is to feed their machine AI and keep you from making wrong-think.
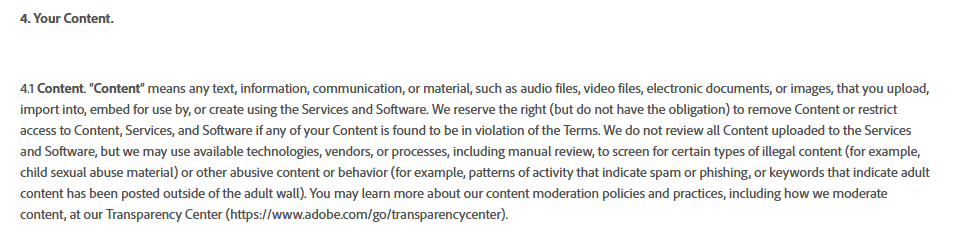
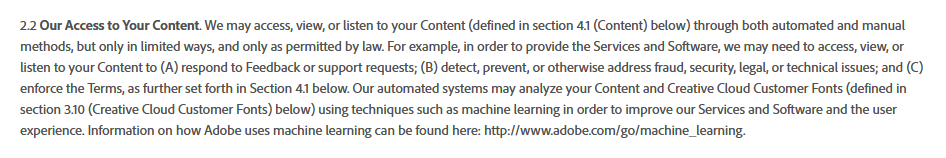
-
The Anglo empire perfected the art of covert control in the colonies over the centuries, building on foundational works by the Jesuits and others. They use a wide range divide & conquer techniques, like psyops, blackmail, controlled opposition, disinformation and more.
-
From Mahatma Gandhi to Julian Assange, one rule holds true: If a "dissident" receives significant attention from the hegemonic mainstream media, even if the coverage is negative, it's very likely they're part of a controlled opposition in an elaborate psyop. Real dissent disappears quickly & silently.
When ever you had enough of getting psyopped every single day by increasingly insane actors & AI weapons, you are free to join the revolution: Turn off your devices and turn to nature - the greatest psyop of all time.

-
Early covert human augmentation programs, utilizing biotech techniques like genetic engineering to enhance intellect, were deemed successful & widely adopted among elite children. However, these programs resulted in noticeable side effects, including severe personality disorders.
-
FearML
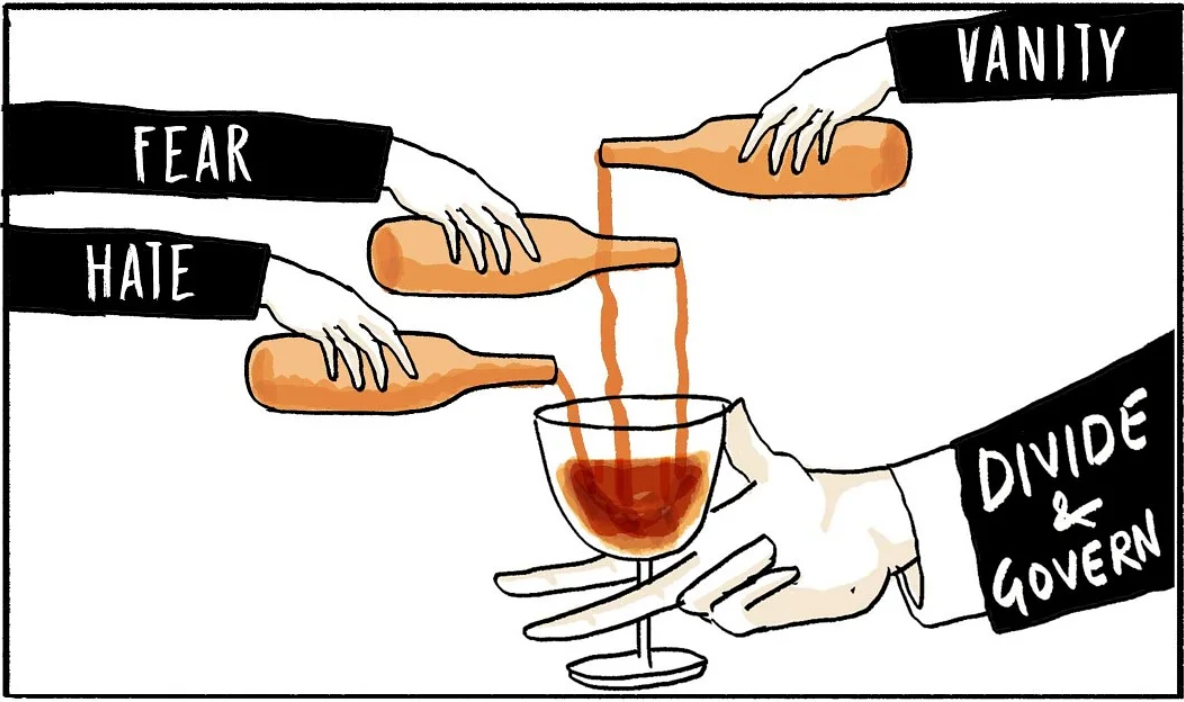
Many years ago the agencies trained a multimodal machine learning model on a massive private dataset, which with high accuracy could predict fear: who is fearful of what & how much, how to make them more fearful with which messages on what channel, etc. It was/is a great success
Once the had perfected AI generated audio/visual media all those years ago, they combined it with their massive media distribution net & digital twin simulation of global society to fuel a game-theoretic, self-optimizing divide & conquer social engineering machine.
-
Articles stating Linus Torvalds joined NSA in 1994 are spreading malicious disinformation. He joined in 1988.



#OpenSource #InfoSec #Cryptocracy #Military #Technology #Comedy #Comment
-
To conduct and support high tech genocide with unfettered brutality & simultaneously babble something about the rise of "artificial super intelligence", is a clear sign of societal stupidity & accelerating degeneration.

-
And the genocide continues..
“More children have been killed by Israel in Gaza than have been killed in all armed conflicts globally, every year, over the past four years.” —Save the Children President and CEO, Janti Soeripto
“In the past month, Israel has bombed Palestine, Lebanon, Egypt and Syria, all the while claiming it’s the victim.” —Irish MEP Clare Daly
And 500 similarly atrocious headlines in the past month.
-
The largest coat of arms of the Supreme Headquarters Allied Powers Europe whose slogan is “ SURVEILLANCE IS THE PRICE OF FREEDOM ”

-
To send material to Cryptome "anonymously":
- Consider that the odds are very high that Cryptome or any other disclosure initiative (anonymizer, leak site, paste, doc-drop, torrent) is a deception operation, witting or unwitting, and avoid their use.
- Protect yourself and never trust any method proposed by a receiver of your material. Never believe assurances of privacy and security for it is customary to deceive about them, witting or unwitting, and inevitable failures are never fully admitted.
- Presume there are no secure means to anonymously transmit online due to the basic design of the Internet to minutely track transmitted data despite illusory promises of anonymizing, cloaking and hiding services.
- Presume undisclosed sysadmin surveillance throughout the online transmittal path.
- Presume there are no fully secure means to encrypt digital material due to the unbridgeable gap between programming limitations of digital data and the engineering indequacies of analog devices to handle it.
- Presume every program, device and system has a traceable embedded unique ID or electromagnetic performance signature.
- If a host is used, run a series of test submssions of provocative but benign material to see what happens. Place "dye markers" in the material to trace its movement. Expect tampering, ruse, subterfuge, false assurance.
- "Not traceable to you," repeated below, is the hardest part only you can do.
-

An alternative, independent intelligence-gathering network run by the Secret Intelligence Service prior to World War II in parallel to, but in isolation from, the conventional Passport Control Offices. Z personnel usually operated under commercial or journalistic cover across Europe. They were directed from offices in Bush House, on the Strand, and were attached to such businesses as Geoffrey Duveen & Co., Alexander Korda’s London Films, and a travel company. In addition, Z’s chief, Claude Dansey, succeeded in recruiting many of his personal contacts, among them some well-known foreign correspondents such as Geoffrey Cox, Frederick Voight, and Eric Gedye.
In September 1939, Z personnel were instructed to make themselves known to the local passport control officer (PCO), wherever they were, and to continue their intelligence-gathering activities in tandem. In reality many PCOs were skeptical about the quality of Z personnel and the reliability of their networks. When Capt. Sigismund Best was abducted at Venlo in November 1939, it was assumed that whatever advantage had been achieved by the Z Organisation had been compromised permanently.
Siegmund George Warburg has worked under cover for the Z Organisation In the period immediately before the Second World War. He reported from Switzerland on his regular meetings with Hjalmar Schacht, then the president of the Nazi German Reichsbank and thus the most powerful German banker.
See as well: Z Special Unit, Use of Z symbol in Russia/Ukraine War
-
Believing that the small elite group controlling the global tech infrastructure—undersea fiber cables, satellites, electricity, etc.—would permit any entity/system to thrive on their network that threatens their monopoly is a widely held yet profoundly misguided fairy tale.
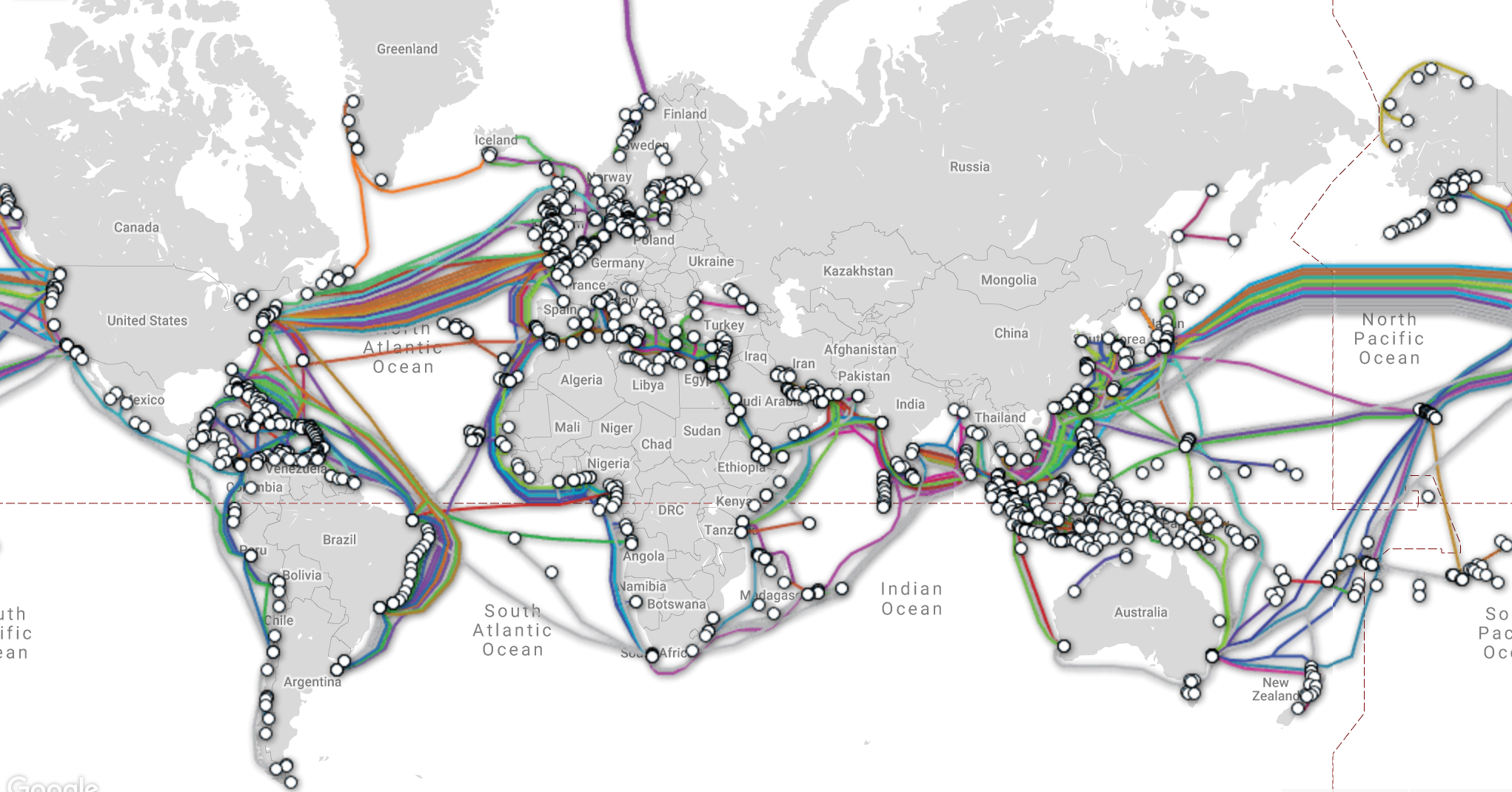
#Comment #Cryptocracy #Internet #Military #Technology #Crypto